ZTNA: Why Organizations Need Cybersecurity Systems That Don’t Leave Loopholes
Historically, cybersecurity has been modeled around a perimeter of trust encompassing trusted network infrastructure, users and devices. However, cybercriminals and malicious actors have been able to exploit this model. Today, organizations need robust cybersecurity systems that don’t leave open loopholes. A zero-trust security framework does just that by eliminating implicit trust and continuously validating every step of digital interaction.
Definition
A cybersecurity strategy, “zero trust,” prohibits access to an enterprise’s digital resources by default. It only provides authorized people and devices with specialized, compartmentalized access to the systems, data, and apps required to perform their tasks. This approach is known as perimeter-less security or zero-trust network architecture (ZTNA).
While it can sound intimidating, implementing a zero-trust strategy is easier than it may seem. But it comes with challenges, including a cultural shift, technical complexity, integration issues and cost.
A zero-trust model can help secure your organization’s network by preventing attackers from lateral movement across your infrastructure. It is accomplished by continuously verifying the identity of users and devices on every request they make, which can stop an attacker from gaining access to critical systems and data.
This security approach also makes it easier to protect the most valuable data in your organization. It includes sensitive data like protected health information, payment card information, intellectual property and other important information.
A zero-trust strategy can be complex, requiring various policies, procedures and technologies. However, a comprehensive zero-trust plan can help prevent breaches and safeguard your organization from growing cyberattacks.
Benefits
Zero trust, also known as de-perimeterization, is a security model that stops all applications and services from communicating until they are verified by their identity attributes—immutable properties that meet predefined trust principles such as authentication and authorization. This approach eliminates the need for traditional perimeter security, limiting the “blast radius” of an attack.
It’s an essential security strategy for modern enterprises. Zero trust is a powerful security platform enabling real-time reaction to attacks. It was created to fulfill the requirements of a decentralized network architecture.
By following the principle of least privilege, zero trust establishes trust through contexts, such as a user’s location, device security posture and application requests. When a user accesses a resource, they must pass authentication and authorization multiple times before gaining full access to the network.
While this security model eliminates many problems plaguing the perimeter, it still requires significant work. In addition to establishing baselines, ZTNA solutions must continually update IP data and implement micro-segmentation and other access control policies to minimize lateral movement within the network and prevent insider attacks.
These tasks can be overwhelming and time-consuming, especially given the complexity of a modern organization’s distributed infrastructure. For this reason, some organizations opt to deploy zero trust on a phased basis, starting with critical assets or test cases of non-critical assets before moving on to the entire network.
Challenges
In a modern network, the traditional security perimeter no longer exists. Instead, workloads must travel across multiple locations and be protected against lateral movement. That means a new model of security needs to be implemented: zero trust.
Unlike the traditional firewall model, zero trust prioritizes security by continuously verifying access before allowing it. It also prioritizes user experience, requiring every user, device, or application to be authenticated and authorized before accessing data.
However, this approach can slow application performance and workflows when users need help identifying themselves or their devices quickly enough. For example, if an employee changes roles and needs access to a new set of files that require updated access credentials, this can create roadblocks in their workflow unless the change is recognized quickly.
While these challenges are common, they can be mitigated by adopting a platform approach that provides unified visibility and control over your identity, data, devices, and applications. That can make achieving a zero-trust system across your organization easier and scale it effectively.
A zero-trust approach can help ensure that your employees are protected against phishing and social engineering attacks, which use a combination of faked login information, malware, or other tactics to gain access to your network. In addition, it can help minimize the damage from cybercriminals who use stolen or compromised credentials to access your network and steal your data.
Implementation
The implementation of zero trust is a shift in how an organization handles security. Historically, organizations have used firewalls to create a perimeter around their network and trusted all users/devices inside the perimeter. This approach works well for entirely local networks, but more is needed to protect against today’s distributed workforce.
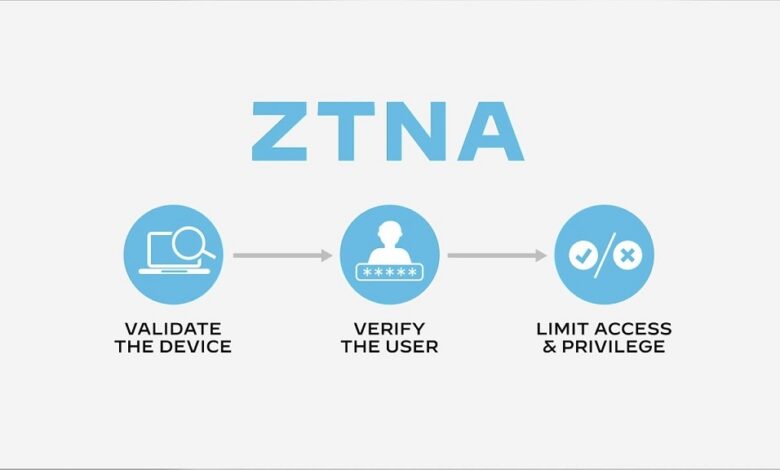
Instead, a zero-trust security model requires all users and devices to be authenticated, authorized and continuously validated for security configuration and posture before being granted or kept access to applications and data. It also eliminates permission sprawl, which can lead to security threats.
Microsegmentation is a critical component of a zero-trust approach to network security. It divides the network into smaller, more secure zones protected by a firewall or filter.
In addition to micro-segmentation, a zero-trust security model relies on device control and multifactor authentication (MFA). MFA demands that users provide at least two pieces of proof, such as their passwords, one-time passwords given to their phones, fingerprint or face recognition data, a security fob, or other things they are aware of, own, or can access.
Ultimately, implementing a zero-trust strategy can be a significant cultural and technical shift, but it can help organizations avoid costly breaches and minimize the impact of an attack. But it can be challenging and time-consuming to implement, and many factors must be considered.